Posted by: @merakisimon
We’ve all read the horror stories. Passwords, private photos, corporate data, government secrets. What hasn’t been compromised at some point? Connectivity is so important to us that sometimes we forget we may not be the only ones joined to that café hotspot. Thankfully today many of the services we access are reached over an SSL connection, but a Virtual Private Network (VPN) remains the best way to protect all traffic.
Setup Meraki Client Vpn Windows 10
Do you want access to your resources remotely?- Do your employees work outside of the office?- Do you want RDP to servers from anywhere?. VPN Client Configuration on Z3. This step will allow you to have your smart device, such as an iPhone to have a VPN client.Z3- Teleworker Gateway- Client VPN - “Enabled”.Z3- Teleworker Gateway- Client VPN - Authentication - “Meraki Cloud Authentication”.Z3- Teleworker Gateway- Client VPN - User Management- Add new user- and “Create a username and password”.
Using a VPN in itself is not so hard. An iPhone with VPN configured will simply present a toggle for the user to slide.
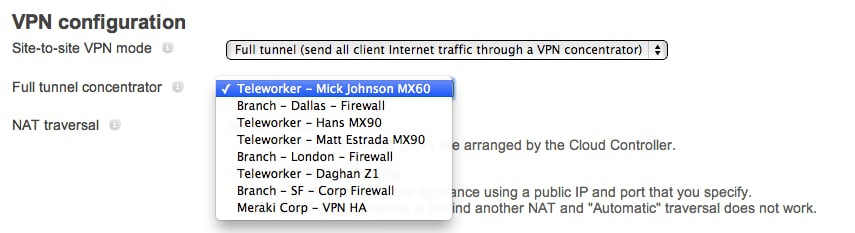
So the issue isn’t connecting to VPN, but configuring it in the first place. Even people who consider themselves ‘technical’ can struggle here, because VPN configuration requires the user to configure several settings. Here’s what the iPhone owner is confronted with when attempting to add a new VPN configuration:
Meraki to the rescue! Customers who deploy one of our powerful MX Security Appliances together with Systems Manager have everything they need to build a turnkey VPN solution in their hands. Among the Security Appliance’s many features are comprehensive site-to-site and client VPN. Pairing an MX with Systems Manager adds a number of powerful security features we call Sentry.
To get things set up, log on to the dashboard and head over to the Client VPN settings page on the MX to which VPN clients will connect. Enable the Client VPN server and then enter the desired settings and then select ‘Systems Manager Sentry VPN Security’. This will open up a new panel as shown here:
In the Sentry VPN section the admin chooses the Systems Manager network (if there is more than one) and the scope of devices which will receive the VPN settings. The usual Systems Manager tags are available here, both static and dynamic, enabling tight control over which devices will be enabled for VPN. Finally, determine whether this should be a full tunnel VPN (Send All Traffic, a good choice when on unfamiliar networks), and any proxy settings before clicking save. That’s all there is to it! Oh, and we can perform the same trick for Mac OS X too and Samsung Knox enabled Android devices.
This truly is simplicity at its best. No need to worry about user configuration, or shared secrets, or server credentials. Everything is automatically pulled from the selected Security Appliance and then pushed out through a profile update to managed clients. The client device will then see the VPN option in settings, and then need only click the toggle to bring the VPN up.

Not ready to purchase a Security Appliance yet? Systems Manager will also allow the manual configuration and deployment of VPN server credentials for any L2TP, PPTP, Cisco IPSec or AnyConnect server.
Sentry is the name we give to a range of security related features which can be used when deploying Systems Manager into an environment with a Meraki network infrastructure. We’ve covered several of these features already on the blog. In this case, Sentry VPN overcomes the biggest obstacle to secure network communications, making it a cinch to set-up, and a trivial option for the end user. Coffee shop productivity just got a lot more secure.
Try Systems Manager on for size by heading over to our website. As with all Meraki solutions, the software is all driven from and accessed via a robust cloud architecture. There’s no hardware required to get started, making it easy to take for a test drive from the comfort of your chair.
Related Posts
Recovering Access to Accounts Protected by Two-Factor Authentication
Two Factor Authentication (TFA) is an important security mechanism, and cannot be disabled by Cisco Meraki without positively identifying the account owner. There are two methods available to ensure access is not lost: a backup phone number (with SMS auth), and a list of one-time codes (with Google Authenticator).
The two methods above are the primary options for disabling or temporarily bypassing two-factor authentication. If these methods cannot be utilized for any reason, the only alternative is to provide proof of identity after contacting Cisco Meraki Technical Support. There are two methods to request removal of SMS and Google Authentication for TFA.
Please note that 2FA removal requests cannot be resolved via our support phone lines. 2FA disablement needs to be requested and processed by the admin email that needs assistance via a Meraki case for security purposes. See steps on recovering access below.
Configure Meraki Vpn
Method 1:
- Open a case by emailing licensing@meraki.com.
- This email must be sent from the email address of the account TFA is to be disabled on.
- It must include the full name of the organization that the account resides in. - A second organization administrator must comment on the case through Dashboard granting approval to disable TFA on the account.
- Email or phone approval is not acceptable for this. The approval must come as a comment on the case.
- This permission can be granted only by an organization administrator with Full access.
Setup Client Vpn Meraki Pc
Method 2:
Alternatively, if a second organization administrator with full access does not exist or is otherwise unavailable:
- Open a case by emailing licensing@meraki.com.
- This email must be sent from the email address of the account TFA is to be disabled on. - Once in communication with a Cisco Meraki Support Specialist, explain that TFA needs to be disabled for the account and provide the requested documentation.
- The Support Operations Specialist will request more information about the organization and its contents and settings to verify the validity of the request.
- Once this step has been completed, a Cisco Meraki Support Specialist will provide you a document which must be signed, notarized, and mailed to Cisco Meraki Headquarters (address found below).
- When this is received by support, it will then be scanned and attached to the case before TFA is disabled.
- It is strongly recommended to send this letter with tracking, in case of postal issues.
- Unless otherwise specified by the Support Ops Team, use the following address format:
Cisco Meraki- Support Operations
500 Terry A Francois Blvd
4th Floor, C/O [SUPPORT OPS SPECIALIST'S NAME]
San Francisco, CA 94158
